hardaware ,networking,firewall,router desktop,switch,server,nas,san,lan,wan software download ,animation knowledge all it and computer knowledge
Your custom script
Friday, 4 December 2015
Friday, 27 November 2015
What are routers?
Routers can connect two or more network segments. These are intelligent network devices that
store information in its routing table such as paths, hops and bottlenecks. With this info, they are
able to determine the best path for data transfer. Routers operate at the OSI Network Layer.
What is point to point link?
It refers to a direct connection between two computers on a network. A point to point connection
does not need any other network devices other than connecting a cable to the NIC cards of both
computers.
What is anonymous FTP?
Anonymous FTP is a way of granting user access to files in public servers. Users that are
allowed access to data in these servers do not need to identify themselves, but instead log in as
an anonymous guest.
What is subnet mask?
A subnet mask is combined with an IP address in order to identify two parts: the extended
network address and the host address. Like an IP address, a subnet mask is made up of 32
bits.
What is the maximum length allowed for a UTP cable?
A single segment of UTP cable has an allowable length of 90 to 100 meters. This limitation can
be overcome by using repeaters and switches.
What is data encapsulation?
Data encapsulation is the process of breaking down information into smaller manageable
chunks before it is transmitted across the network. It is also in this process that the source and
destination addresses are attached into the headers, along with parity checks.
Describe Network Topology
Network Topology refers to the layout of a computer network. It shows how devices and cables
are physically laid out, as well as how they connect to one another.
NETWORKING QUESTION
1) What is a Link?
A link refers to the connectivity between two devices. It includes the type of cables and
protocols used in order for one device to be able to communicate with the other.
2) What are the layers of the OSI reference model?
There are 7 OSI layers: Physical Layer, Data Link Layer, Network Layer, Transport Layer,
Session Layer, Presentation Layer and Application Layer.
3) What is backbone network?
A backbone network is a centralized infrastructure that is designed to distribute different routes
and data to various networks. It also handles management of bandwidth and various channels.
4) What is a LAN?
LAN is short for Local Area Network. It refers to the connection between computers and other
network devices that are located within a small physical location.
5) What is a node?
Q. What are application partitions? When do I use them?
A1) Application Directory Partition is a partition space in Active Directory which an application can use to store that application specific data. This partition is then replicated only to some specific domain controllers.The application directory partition can contain any type of data except security principles (users, computers, groups).**A2) These are specific to Windows Server 2003 domains. An application directory partition is a directory partition that is replicated only to specific domain controllers. A domain controller that participates in the replication of a particular application directory partition hosts a replica of that partition. Only domain controllers running Windows Server 2003 can host a replica of an application directory partition.
Q. Name the AD NCs and replication issues for each NC
Schema NC, *Configuration NC, *
Domain NCSchema NC: This NC is replicated to every other domain controller in
the forest. It contains information about the Active Directory schema, which in
turn defines the different object classes and attributes within Active
Directory.
Q. What is the SYSVOL folder?
The SYSVOL folder is critical
because it contains the domain’s public files. This directory is shared out (as
SYSVOL), and any files kept in the SYSVOL folder are replicated to all other
domain controllers in the domain using the File Replication Service (FRS)—and
yes, that’s important to know on the exam.The SYSVOL folder also contains the
following items:
- The NETLOGON share, which is the location where domain
logon requests are submitted for processing, and where logon scripts can
be stored for client processing at logon time.
- Windows Group Policies
- FRS folders and files that must be available and
synchronized between domain controllers if the FRS is in use. Distributed
File System (DFS), for example, uses the FRS to keep shared data
consistent between replicas.
You can go to SYSVOL folder by
typing : %systemroot%/sysvol on DC.
Q. Where is the AD database held? What other folders are related to AD?
AD Database is saved in
%systemroot%/ntds. You can see other files also in this folder. These are the
main files controlling the AD structure
- ntds.dit
- edb.log
- res1.log
- res2.log
- edb.chk
Q. Can you connect Active Directory to other 3rd-party Directory Services? Name a few options.
Yes you can Connect Active Directory to other 3rd -party Directory Services such as dictonaries used by SAP, Domino etc with the help of MIIS ( Microsoft Identity Integration Server ) you can use dirXML or LDAP to connect to other directories (ie. E-directory from Novell).
Q. What is FRS (File replication services)?
The File Replication Service (FRS) replicates specific files using the same multi-master model that Active Directory uses.
WHAT IS LDAP ?
Short for Lightweight Directory Access Protocol, a set of protocols for accessing information directories. LDAP is based on the standards contained within the X.500 standard, but is significantly simpler. And unlike X.500, LDAP supports TCP/IP, which is necessary for any type of Internet access. Because it’s a simpler version of X.500, LDAP is sometimes called X.500-lite.
Q. How do you verify whether the AD installation is proper?
- An NTFS partition with enough free space
- An Administrator’s username and password
- The correct operating system version
- A NIC
- Properly configured TCP/IP (IP address, subnet mask and
– optional – default gateway)
- A network connection (to a hub or to another computer
via a crossover cable)
- An operational DNS server (which can be installed on
the DC itself)
- A Domain name that you want to use
- Q. How do you verify whether the AD
installation is proper?
- Default containers: These are created automatically
when the first domain is created. Open Active Directory Users and
Computers, and then verify that the following containers are present: Computers,
Users, and ForeignSecurityPrincipals.
- Default domain controllers organizational unit: Open Active
Directory Users and Computers, and then verify this organizational
unit.
- Default-First-Site-Name
- Active Directory database: The Active Directory
database is your Ntds.dit file. Verify its existence in the %System root%\Ntds
folder.
- Global catalog server: The first domain controller
becomes a global catalog server, by default. To verify this item:
- a. Click Start, point to Programs, click Administrative
Tools, and then click Active Directory Sites and Services.
- b. Double-click Sites to expand it, expand Servers,
and then select your domain controller.
- c. Double-click the domain controller to expand the
server contents.
- d. Below the server, an NTDS Settings object is
displayed. Right-click the object, and then click Properties.
- e. On the General tab, you can observe a global
catalog check box, which should be selected, by default.
- Root domain: The forest root is created when the first domain
controller is installed. Verify your computer network identification in My
Computer. The Domain Name System (DNS) suffix of your computer should match
the domain name that the domain controller belongs to. Also, ensure that your
computer registers the proper computer role. To verify this role, use the net
accounts command. The computer role should say “primary” or “backup” depending
on whether it is the first domain controller in the domain.
- Shared system volume: A Windows 2000 domain controller should have a shared
system volume located in the %Systemroot%\Sysvol\Sysvol folder. To verify this
item, use the net share command. The Active Directory also creates two
standard policies during the installation process: The Default Domain policy
and the Default Domain Controllers policy (located in the
%Systemroot%\Sysvol\Domain\Policies folder). These policies are displayed as
the following globally unique identifiers (GUIDs):
- {31B2F340-016D-11D2-945F-00C04FB984F9}
representing the Default Domain policy
- {6AC1786C-016F-11D2-945F-00C04fB984F9} representing the Default Domain
Controllers policy
- SRV resource records: You must have a DNS server installed and configured for
Active Directory and the associated client software to function correctly.
Microsoft recommends that you use Microsoft DNS server, which is supplied with
Windows 2000 Server as your DNS server. However, Microsoft DNS server is not
required. The DNS server that you use must support the Service Resource Record
(SRV RR) Requests for Comments (RFC) 2052, and the dynamic update protocol (RFC
2136). Use the DNS Manager Microsoft Management Console (MMC) snap-in to verify
that the appropriate zones and resource records are created for each DNS zone.
Active Directory creates its SRV RRs in the following folders:
- _Msdcs/Dc/_Sites/Default-first-site-name/_Tcp
- _Msdcs/Dc/_Tcp
- In these locations, an SRV RR is
displayed for the following services:
- o _kerberos
- o _ldap
Q. Minimum requirement to install Win 2008 AD?
- An NTFS partition with enough free space
- An Administrator’s username and password
- The correct operating system version
- A NIC
- Properly configured TCP/IP (IP address, subnet mask and
– optional – default gateway)
- A network connection (to a hub or to another computer
via a crossover cable)
- An operational DNS server (which can be installed on
the DC itself)
- A Domain name that you want to use
Q. What are the protocols used by AD?
Because Active Directory is based on
standard directory access protocols, such as Lightweight Directory Access
Protocol (LDAP) version 3, and the Name Service Provider Interface (NSPI), it
can interoperate with other directory services employing these protocols.
LDAP is the directory access
protocol used to query and retrieve information from Active Directory. Because
it is an industry-standard directory service protocol, programs can be
developed using LDAP to share Active Directory information with other directory
services that also support LDAP.
The NSPI protocol, which is used by
Microsoft Exchange 4.0 and 5.x clients, is supported by Active Directory
to provide compatibility with the Exchange directory.
Q. What are the components of Active Director?
Object:
An object is any specific item that can be cataloged in Active Directory. Examples of objects include users, computers, printers, folders, and files. These items are classified by a distinct set of characteristics, known as attributes. For example, a user can be characterized by the username, full name, telephone number, email address, and so on. Note that, in general, objects in the same container have the same types of attributes but are characterized by different values of these attributes. The Active Directory schema defines the extent of attributes that can be specified for any object.
Classes
The Active Directory service, in turn, classifies objects into classes. These classes are logical groupings of similar objects
Schemas
The schema is a set of rules that define the classes of objects and their attributes that can be created in Active Directory. It defines what attributes can be held by objects of various types, which of the various classes can exist, and what object class can be a parent of the current object class. For example, the User class can contain user account objects and possess attributes such as password, group membership, home folder, and so on.When you first install Active Directory on a server, a default schema is created, containing definitions of commonly used objects and properties such as users, computers, and groups. This default schema also contains definitions of objects and properties needed for the functioning of Active Directory.
Global catalog
A global catalog server is a
domain controller that has an additional duty—it maintains a global catalog. A
global catalog is a master, searchable database that contains information about
every object in every domain in a forest. The global catalog contains a
complete replica of all objects in Active Directory for its host domain, and
contains a partial replica of all objects in Active Directory for every other
domain in the forest.
- A global catalog server performs two important
functions:
- Provides group membership information during logon and
authentication
- Helps users locate resources in Active Directory
SITES-
Sites
By contrast to the logical grouping of Active Directory into forests, trees, domains, and OUs, Microsoft includes the concept of sites to group together resources within a forest according to their physical location and/or subnet. A site is a set of one or more IP subnets, which are connected by a high-speed, always available local area network (LAN) link. Figure 1-5 shows an example with two sites, one located in Chicago and the other in New York. A site can contain objects from more than one tree or domain within a single forest, and individual trees and domains can encompass more than one site. The use of sites enables you to control the replication of data within the Active Directory database as well as to apply policies to and computers or delegate
administrative control to these objects within a single physical location. In
addition, sites enable users to be authenticated by domain controllers in the
same physical location rather than a distant location as often as possible. You
should configure a single site for all work locations connected within a
high-speed, always available LAN link and designate additional sites for
locations separated from each other by a slower wide area network (WAN) link.
Using sites permits you to configure Active Directory replication to take
advantage
of the high-speed connection. It
also enables users to connect to a domain controller using a reliable,
high-speed connection.
all users DOMAIN CONTROLLER
Domain Controllers
Any server on which you have
installed Active Directory is a domain controller. These servers
authenticate all users logging on to the domain in which they are located, and
they also serve as centers from which you can administer Active Directory in
Windows Server 2008. A domain controller stores a complete copy of all objects
contained within the domain, plus the schema and configuration information
relevant to the forest in which the domain is located. Unlike Windows NT, there
are no primary or backup domain controllers. Similar to Windows 2000 and
Windows Server 2003, all domain controllers hold a master, editable copy of the
Active Directory database.
Every domain must have at least one
DC. A domain may have more than one DC; having more than one DC provides the
following benefits:
- Fault tolerance: If one domain controller goes down, another one is
available to authenticate logon requests and locate resources through the
directory.
- Load balancing: All domain controllers within a site participate
equally in domain activities, thus spreading out the load over several
servers. This configuration optimizes the speed at which requests are
serviced.
Organizational Unit:An organizational unit (OU) is a
container used to organize objects within one domain into logical
administrative groups. An OU can contain objects such as user accounts, groups,
computers, printers, applications, shared folders, and other OUs from the same
domain. OUs are represented by a folder icon with a book inside. The Domain
Controllers OU is created by default when Active Directory is installed to hold
new Microsoft Windows Server 2003 domain controllers. OUs can be added to other
OUs to form a hierarchical structure; this process is known as nesting OUs.
Each domain has its own OU structure—the OU structure within a domain is
independent of the OU structures of other domains.There are three reasons for defining
an OU:
- To delegate administration – In the Windows Server 2003
operating system, you can delegate administration for the contents of an
OU (all users, computers, or resource objects in the OU) by granting
administrators specific permissions for an OU on the OU’s access control
list.
- To administer Group Policy
- To hide object
Physical Components of Active
DirectoryThere are two physical components of
Active Directory:
- Domain Controllers
- Sites
Q. What are the physical components of active directory? Logical Components of Active Directory
In creating the hierarchical database structure of Active Directory, Microsoft facilitated locating resources such as folders and printers by name rather than by physical location. These logical building blocks include domains, trees, forests, and OUs. The physical location of objects within Active Directory is represented by including all objects in a given location in its own site. Because a domain is the basic unit on which Active Directory is built, the domain is introduced first; followed by trees and forests (in which domains are located); and then OUs, which are containers located within a domain.
ACTIVE DIRECTERY-
Q. What is Active Directory?
Active Directory is the directory service used by Windows 2000. A directory
service is a centralized, hierarchical database that contains information about
users and resources on a network. In Windows 2000, this database is called the Active
Directory data store. The Active Directory data store contains information
about various types of network objects, including printers, shared folders,
user accounts, groups, and computers. In a Windows 2000 domain, a read/write
copy of the Active Directory data store is physically located on each domain
controller in the domain.
Three primary purposes of Active
Directory are:
- · To provide user logon and authentication services
- · To enable administrators to organize and manage user
accounts groups, and network resources
- · To enable authorized users to easily locate network
resources, regardless of where they are located on the network
A directory service consists
of two parts—a centralized, hierarchical database that contains information
about users and resources on a network, and a service that manages the database
and enables users of computers on the network to access the database. In
Windows 2008, the database is called the Active Directory data store, or
sometimes just the directory. The Active Directory data store contains
information about various types of network objects, including printers, shared
folders, user accounts, groups, and computers. Windows 2000 Server computers
that have a copy of the Active Directory data store, and that run Active
Directory are called domain controllers. In a Windows 2008 domain, a
read/write copy of the Active Directory data store is physically located on
each domain controller in the domain.
WHAT IS FOREST ?
Forests
A forest is a grouping or
hierarchical arrangement of one or more separate, completely independent domain
trees. As such, forests have the following characteristics:
- All domains in a forest share a common schema.
- All domains in a forest share a common global catalog.
- All domains in a forest are linked by implicit two-way
transitive trusts.
Trees in a forest have different
naming structures, according to their domains. Domains in a forest operate
independently, but the forest enables communication across the entire
organization.
WHAT IS TREE ?
Trees
A tree is a group of domains
that shares a contiguous namespace. In other words, a tree consists of a parent
domain plus one or more sets of child domains whose name reflects that of a
parent. For example, a parent domain named examcram.com can include child
domains with names such as products.examcram.com, sales.examcram.com, and
manufacturing.examcram.com. Furthermore, the tree structure can contain
grandchild domains such as america.sales.examcram.com or
europe.sales.examcram.com, and so on, as shown in Figure 1-2. A domain called
que.com would not belong to the same tree. Following the inverted tree concept
originated by X.500, the tree is structured with the parent domain at the top
and child domains beneath it. All domains in a tree are linked with two-way,
transitive trust relationships; in other words, accounts in any one domain can
access resources in another domain and vice versa.
WHAT IS DOMAIN ?
Domain:
A domain is a logical
grouping of networked computers in which one or more of the computers has one
or more shared resources, such as a shared folder or a shared printer, and in
which all of the computers share a common central domain directory database
that contains user account security information. One distinct advantage of
using a domain, particularly on a large network, is that administration of user
account security for the entire network can be managed from a centralized
location. In a domain, a user has only one user account, which is stored in the
domain directory database. This user account enables the user to access shared
resources (that the user has permissions to access) located on any computer in
the domain
Active Directory domains can hold
millions of objects, as opposed to the Windows NT domain structure, which was
limited to approximately 40,000 objects. As in previous versions of Active
Directory, the Active Directory database file (ntds.dit) defines the domain.
Each domain has its own ntds.dit file, which is stored on (and replicated
among) all domain controllers by a process called multimaster replication.
The domain controllers manage the configuration of domain security and store
the directory services database. This arrangement permits central administration
of domain account privileges, security, and network resources. Networked
devices and users belonging to a domain validate with a domain controller at
startup. All computers that refer to a specific set of domain controllers make
up the domain. In addition, group accounts such as global groups and domain
local groups are defined on a domain-wide basis.
Monday, 2 November 2015
Wednesday, 21 October 2015
WHAT IS VIRUS ?
Ans- a computer virus is without your knowledge loaded on your computer .all computer virus is manmade .virus is harmfull our pc
WHAT IS SUBNETTING ?
Ans- subnatting is process in which larger ip network is broken into seprated and smaller network
Sunday, 11 October 2015
Tuesday, 8 September 2015
AUTOMIC PRIVATE IP ADDRESSING (APIPA)
APIPA-
( AUTOMATIC PRIVATE IP ADDRESSING IS A ADDRESSING) FEATURE FOR SINGLE NETWORK SEGMENT. WHENEVER A COMPUTER RUNNING WINDOWS HAS BEEN CONFIGURED OBTAIN ON IP ADDRESS AUTOMATICALLY AND WHEN D.H.C.P. OR ETHERNET CONFIGURATION
IS AVAILABLE THE COMPUTER USES APIPA TO ASSIGN IN THE RANGE OF
169.254.0.1 TO 169.254.255.254
PRIVATE ADDRESS
1.ACCORDING TO RFC-1918
2.ORGANIZATIONS MAKE USE OF THE PRIVATE INTERNET ADDRESS SPACE FOR HOSTS THAT REQUIRE IP CONNECTVITY
WITH IN THEIR ENTERPRISE NETWORK BUT DO NOT REQUIRE EXTERNAL CONNECTIONS TO THE GLOBAL INTERNET
3.CLASS A: 10.0.0.0
4.CLASS B :172.16.0.0,172.31.0.0
5CLASS C :192.168.0.0,192.168.255.0
SOME FULL FORMS-
RFC=REQUEST FORM COMMENTS
AWG=AMERICAN WIRED GAUGE
2.ORGANIZATIONS MAKE USE OF THE PRIVATE INTERNET ADDRESS SPACE FOR HOSTS THAT REQUIRE IP CONNECTVITY
WITH IN THEIR ENTERPRISE NETWORK BUT DO NOT REQUIRE EXTERNAL CONNECTIONS TO THE GLOBAL INTERNET
3.CLASS A: 10.0.0.0
4.CLASS B :172.16.0.0,172.31.0.0
5CLASS C :192.168.0.0,192.168.255.0
SOME FULL FORMS-
RFC=REQUEST FORM COMMENTS
AWG=AMERICAN WIRED GAUGE
MAKE CROSS CABLE
CROSS CABLE USED FOR SAME USED
(@).COMPUTER TO COMPUTER, SWITCH TO SWITCH, ROUTER TO ROUTER
1.ORANGE/WHITE 1.GREEN/WHITE
2.ORANGE 2.GREEN
3.GREEN/WHITE 3.ORANGE/WHITE
4.BLUE 4.BLUE
5.BLUE/WHITE 5.BLUE/WHITE
6.GREEN 6.ORANGE
7.BROWN/WHITE 7.BROWN/WHITE
8.BROWN 8.BROWN
(@).COMPUTER TO COMPUTER, SWITCH TO SWITCH, ROUTER TO ROUTER
1.ORANGE/WHITE 1.GREEN/WHITE
2.ORANGE 2.GREEN
3.GREEN/WHITE 3.ORANGE/WHITE
4.BLUE 4.BLUE
5.BLUE/WHITE 5.BLUE/WHITE
6.GREEN 6.ORANGE
7.BROWN/WHITE 7.BROWN/WHITE
8.BROWN 8.BROWN
BROADCAST ADDRESS
1. BROADCAST GOES TO EVERY HOST WITH A PARTICULAR NETWORK ID NUMBER
2.AN IP ADDRESS THAT ENDS WITH BINARY IS IN ALL HOST BITS IS RESERVED FOR THE DIRECTED BROADCAST ADDRESS
3.AN IP ADDRESS WITH BINARY IS IN ALL NETWORK BITS IS RESERVED FOR THE LOCAL BROADCAST ADDRESS
2.AN IP ADDRESS THAT ENDS WITH BINARY IS IN ALL HOST BITS IS RESERVED FOR THE DIRECTED BROADCAST ADDRESS
3.AN IP ADDRESS WITH BINARY IS IN ALL NETWORK BITS IS RESERVED FOR THE LOCAL BROADCAST ADDRESS
NETWORK ADDRESS
1.NETWORK ADDRESS PROVIDE A CONVENIENT WAY TPO REFER TO ALL OF THE ADDRESS ON A PARTICULAR NETWORK OR SUBNETWORK
2.TWO HOSTS WITH DEFFERING NETWORK ADDRESS REQUIRE A DEVICE TYPICALLY ROUTER IN ORDER TO COMMUNICATE
3. AN IP ADDRESS THAT ENDS WITH BINARY IN ALL HOST BITS IS RESERVED FOR THE NETWORK ADDRESS
2.TWO HOSTS WITH DEFFERING NETWORK ADDRESS REQUIRE A DEVICE TYPICALLY ROUTER IN ORDER TO COMMUNICATE
3. AN IP ADDRESS THAT ENDS WITH BINARY IN ALL HOST BITS IS RESERVED FOR THE NETWORK ADDRESS
IP ADDRESS CLASSES : SUMMARY
1. 1.0.0.0-127.0.0.0 :CLASS A
2. 127.0.0.0 : LOOP BACK ADAPTER
3. 128.0.0.0 -191.255.0.0 :CLASS B
4. 192.0.0.0-223.225.255.0 :CLASS C
5. 224.0.0.0 < 240.0.0.0 :CLASS D (MULTICAST)
6. >=240.0.0.0 : CLASS E (RESERVED)
2. 127.0.0.0 : LOOP BACK ADAPTER
3. 128.0.0.0 -191.255.0.0 :CLASS B
4. 192.0.0.0-223.225.255.0 :CLASS C
5. 224.0.0.0 < 240.0.0.0 :CLASS D (MULTICAST)
6. >=240.0.0.0 : CLASS E (RESERVED)
CLASS C
1. THE FIRST 3 BITS OF A CLASS C ADDRESS IS ALWAYS 110
2. THE FIRST THREE OCTES TO IDENTIFY THE NETWORK PAST OF THE ADDRESS
3.POSSIBLE NETWORK ADDRESS FROM 192.0.0.0 T0 223.255.255.0
4. THE REMAINING LAST OCTES CAN BE USED FOR THE HOST PARTION OF THE ADDRESS
5.CLASS C NETWORK HAVE UP TO 254 P0SSIBLE IP ADDRESS
CLASS B
1. THE FIRST 2 BITS OF A CLASS B ADDRESS IS ALWAYS 10
2.THE FIRST TWO OCTES TO IDENTIFY THE NETWORK PAST OF THE ADDRESS
3.POSSIBLE NETWORK ADDRESS FROM 128.0.0.0 T0 191.255.0.0
4.THE REMAINING TWO OCTES CAN BE USED FOR THE HOST PARTION OF THE ADDRESS
5.CLASS B NETWORK HAVE UP 65.534 POSSIBLE IP ADDRESS
2.THE FIRST TWO OCTES TO IDENTIFY THE NETWORK PAST OF THE ADDRESS
3.POSSIBLE NETWORK ADDRESS FROM 128.0.0.0 T0 191.255.0.0
4.THE REMAINING TWO OCTES CAN BE USED FOR THE HOST PARTION OF THE ADDRESS
5.CLASS B NETWORK HAVE UP 65.534 POSSIBLE IP ADDRESS
Monday, 7 September 2015
IP ADDRESS CLASSES :A
1.THE FIRST BIT OF A ADDRESS IS ALWAYS 0
2. THE FIRST 8 BITS TO IDENTIFY THE NETWORK PAST OF THE ADDRESS
3.POSSIBLE NETWORK ADDRESS FROM
1.0.0.0 TO 127.0.0.0
4. THE REMAINING THREE OCTES CAN BE USED FOR THE HOST PARTION OF THE N ETWORK
5. EACH CLASS A NETWORK HAVE UP TO
16,7,77,214 POSSIBLE IP ADDRESS
2. THE FIRST 8 BITS TO IDENTIFY THE NETWORK PAST OF THE ADDRESS
3.POSSIBLE NETWORK ADDRESS FROM
1.0.0.0 TO 127.0.0.0
4. THE REMAINING THREE OCTES CAN BE USED FOR THE HOST PARTION OF THE N ETWORK
5. EACH CLASS A NETWORK HAVE UP TO
16,7,77,214 POSSIBLE IP ADDRESS
DIFFERENT CLASS ADDRESS RESERVE
1.DIFFERENT AMOUNTS OF BITS FOR THE NETWORK AND HOST PARTIONS
2.PROVIDE THE FLEXIBILITY REQUIRED TO SUPPORT DIFFERENT SIZE NETWORK
2.PROVIDE THE FLEXIBILITY REQUIRED TO SUPPORT DIFFERENT SIZE NETWORK
BITS ON THE IP ADDRESS :-
1.NETWORK BITS:-
1. IDENTIFIES NETWORK ID
2. IDENTIFIES CLASS OF THE IP ADDRESS
3. ALL OF BITS ARE 0: NOT ALLOWED
2.HOST BITS:-
1. IDENTIFIES HOST ID
2.ALL OF BITS ARE 0:RESERVED FOR NETWORK ADDRESS
3.ALL OF BITS ARE 1: RESERVED FOR BROADCAST ADDRES
NETWORK ID :-
1. ASSIGNED BY INTERNET NETWORK INFORMATION CENTER
2.ASSIGNED BY UPPER ORGANIZATION
3. IDENTIFIES THE NETWORK TO WHICH A DEVICE IS ATTACHED
2.ASSIGNED BY UPPER ORGANIZATION
3. IDENTIFIES THE NETWORK TO WHICH A DEVICE IS ATTACHED
IP ADDRESS & SUBNETTING
IP ADDRESS-
1. NETWORK LAYER ADDRESS ARE 32 BITS LONG
2.THE ARE PRESENTED AS FOUR OCTCTS IN DOTTED DECIMAL FORMAT
3.THE IP ADDRESS HAS TWO COMPONENTS NETWORK ID AND HOST ID
1. NETWORK LAYER ADDRESS ARE 32 BITS LONG
2.THE ARE PRESENTED AS FOUR OCTCTS IN DOTTED DECIMAL FORMAT
3.THE IP ADDRESS HAS TWO COMPONENTS NETWORK ID AND HOST ID
Thursday, 3 September 2015
Tuesday, 1 September 2015
3.PROXY SERVER
1.ISOLUTS INTERNAL NETWORK COMPUTERS FROM THE INTERNET
2.THE USER FIRST ACCESS THE INTERNET AND RETRIEVES THE REQUESTED WEB PAGE OR DOCUMENT THE USER THEN GETS A COPY OF THAT PAGE FROM THE PROXY SERVER
2.THE USER FIRST ACCESS THE INTERNET AND RETRIEVES THE REQUESTED WEB PAGE OR DOCUMENT THE USER THEN GETS A COPY OF THAT PAGE FROM THE PROXY SERVER
2 GATEWAY
1.CONNECT NETWORK WITH DIFFRENT PROTOCOL LIKE TCP/IP NETWORK AND IPX/SPX NETWORK
2.ROUTERS AND GATEWAYS OFTEN REFER TO THE SAME DEVICE
Monday, 24 August 2015
ADDITIONAL NETWORK HARDWARE DEVICES
*NETWORK INTERFACE CARD -
+PUTS THE DATA INTO PACKETS TRANSMITS PACKETA ON TO THE NETWORK
+MAY BE WIRED OR WIRELESS
ROUTER
*A DEVICE THAT CONNECTS ANY NUMBER OF LANS
*USES STANDARDIZED PROTOCOL TO MOVE PACKET EFFICIENTLY TO THEIR DESTINATION.
*MORE SOPHISTICATED THEN BRIDGES CONNECTING NETWORK OF DIFFERENT TYPES (FOR EXAMPLE STAR AND RING)
*FORWARDS DATA DEPENDING ON THE NETWORK ADDRESS (IP) NOT THE HARDWARE (MAC) ADDRESS
*ROUTERS ARE THE ONLY ONE OF THESE FOUR DEVICES THAT WILL ALLOW YOU TO SHARE A SINGLE IP ADDRESS AMONG MULTIPLE NETWORK
*RESIDES ON LAYER 3 OF THE OSI MODEL
`
*USES STANDARDIZED PROTOCOL TO MOVE PACKET EFFICIENTLY TO THEIR DESTINATION.
*MORE SOPHISTICATED THEN BRIDGES CONNECTING NETWORK OF DIFFERENT TYPES (FOR EXAMPLE STAR AND RING)
*FORWARDS DATA DEPENDING ON THE NETWORK ADDRESS (IP) NOT THE HARDWARE (MAC) ADDRESS
*ROUTERS ARE THE ONLY ONE OF THESE FOUR DEVICES THAT WILL ALLOW YOU TO SHARE A SINGLE IP ADDRESS AMONG MULTIPLE NETWORK
*RESIDES ON LAYER 3 OF THE OSI MODEL
`
REAPEATER
*USED TO BOOST THE SIGNAL BETWEEN TWO CABLE SEGMENTS OR WIRELESS ACCESS POINTS.
*CAN NOT CONNECT DIFFERENT NETWORK ARCHITECTURE.
*DOES NOT SIMPLY AMPLIFY THE SIGNAL IT REGENERATES THE PACKET AND RETIMES THEM.
*RESIDES ON LAYER 1 OF THE OSI MODEL
*CAN NOT CONNECT DIFFERENT NETWORK ARCHITECTURE.
*DOES NOT SIMPLY AMPLIFY THE SIGNAL IT REGENERATES THE PACKET AND RETIMES THEM.
*RESIDES ON LAYER 1 OF THE OSI MODEL
BRIDGE
*CONNECTS TWO LAN AND FORWARD FOTR FILTER DATA PACKETS BETWEEN THEM.
*CREATES AN EXTENTED NETWORK IN WHICH ANY TWO WORKSTATIONS ON THE LINKED LAN CAN SHARE DATA.
*TRANSPORT TO PROTOCOL AND TO HIGHER LEVEL DEVICES LIKE RATES.
*FORWARD DATA DEPENDING ON THE HARDWARE (MAC) ADDRESS NOT THE NETWORK ADDRESS (IP)
*RESIDES ON A LAYER 2 THE OSI MODEL
*CREATES AN EXTENTED NETWORK IN WHICH ANY TWO WORKSTATIONS ON THE LINKED LAN CAN SHARE DATA.
*TRANSPORT TO PROTOCOL AND TO HIGHER LEVEL DEVICES LIKE RATES.
*FORWARD DATA DEPENDING ON THE HARDWARE (MAC) ADDRESS NOT THE NETWORK ADDRESS (IP)
*RESIDES ON A LAYER 2 THE OSI MODEL
SWITCH
*SPILT LARGE NETWORK INTO SMALL SEGMENTS DESCRASSING THE NUMBER OF USER SHARING THE SAME NETWORK RESOURCES AND BANDWIDTH
*UNDERSTANDS WHEN TWO DEVICES WANT TO TALK TO EACH OTHER ,AND GIVES THEM A SWITCH A CONNECTION
*HELP PREVENT DATA COLLISIONS AND REDUCE NETWORK CONGESTION IN CREASING NETWORK PERFORMANCE
*MOST HOME USER GET VERY LITTLE IT ANY ALL VANTAGE FROM SWITCHES EVEN WHEN SHARING A BROADBAND CONNECTION
*RESIDES ON A LAYER2 THE OSI MODEL
*UNDERSTANDS WHEN TWO DEVICES WANT TO TALK TO EACH OTHER ,AND GIVES THEM A SWITCH A CONNECTION
*HELP PREVENT DATA COLLISIONS AND REDUCE NETWORK CONGESTION IN CREASING NETWORK PERFORMANCE
*MOST HOME USER GET VERY LITTLE IT ANY ALL VANTAGE FROM SWITCHES EVEN WHEN SHARING A BROADBAND CONNECTION
*RESIDES ON A LAYER2 THE OSI MODEL
Saturday, 22 August 2015
HUB
* an unintelligent network device that sends one signal to all of the stations connected to it
*traditionaly hubs are used for star topology network but they are often used with other configuration to make it easy to add and remove computers without bringing down the network
*all computer devices are competing for attention
because if takes the data that comes into a part and sends it out all the poot i hub
*traditionaly hubs are used for star topology network but they are often used with other configuration to make it easy to add and remove computers without bringing down the network
* hub work on layer 1 of the osi model
BROADCAST TRANSMISSION
BROADCAST TRANSMISSION-
in broadcast transmission a simple data packet is copied and set to spacific (ALL) destination on the Network
BROADCAST PROCESS-
1.the source address the packet with the broadcast address
2.the packet is sent into the network
3.the network copies
the packet
4. the packet copies are delivered to all destination on the network
in broadcast transmission a simple data packet is copied and set to spacific (ALL) destination on the Network
BROADCAST PROCESS-
1.the source address the packet with the broadcast address
2.the packet is sent into the network
3.the network copies
the packet
4. the packet copies are delivered to all destination on the network
2.MULTICAST TRANSMISSION
In Multicast Transmission a single Data Packet is copied and send to specific destination the network
MULTICAST PROCESS-
1.The Source Address The Packet Using Multicast Address
2.The Packet is Sent into The Network
3.The Network Copies The Packet
4.A Copy is Delivered To each destination That is include in the Multicast
MULTICAST PROCESS-
1.The Source Address The Packet Using Multicast Address
2.The Packet is Sent into The Network
3.The Network Copies The Packet
4.A Copy is Delivered To each destination That is include in the Multicast
FIBER OBTIC
SC-Subscriber connectr
ST-Strait Tips
Fiber Obtic Cables are The latest development in cabling Technology They Are Constructed From obtical Glasses.There is central glass filament calied the core and surrounding layers of cladding
buffer coating strengthening materials and outer jacket
information is transmitted by wavelength of light This is accomplishrd through devices that convent electrical signal into repiod pulses of either LED Laser Light Fiber obtic Cables After several advantage including
1.High Bandwidth capacity (many gigabite per second)
2.Longer Distance Between Device (from 2 t0 over 60 km)
3. immunity to electromegnatic interferences
Fiber obtic Cables are widely Used in WAN for both Voice and Data communications. The primary barrier to their widespread use in LAN is the Cost of electronic
ST-Strait Tips
Fiber Obtic Cables are The latest development in cabling Technology They Are Constructed From obtical Glasses.There is central glass filament calied the core and surrounding layers of cladding
buffer coating strengthening materials and outer jacket
information is transmitted by wavelength of light This is accomplishrd through devices that convent electrical signal into repiod pulses of either LED Laser Light Fiber obtic Cables After several advantage including
1.High Bandwidth capacity (many gigabite per second)
2.Longer Distance Between Device (from 2 t0 over 60 km)
3. immunity to electromegnatic interferences
Fiber obtic Cables are widely Used in WAN for both Voice and Data communications. The primary barrier to their widespread use in LAN is the Cost of electronic
2.Shieled twisted Pair
STP cable is also Network is also used for data Network is orginess IBM to can N/w
it shielding arrowd greater tollvence for protection From EMI such as from florocence light picture and electric motor
it shielding arrowd greater tollvence for protection From EMI such as from florocence light picture and electric motor
TP(TWISTED PAIR CABLE)
(1).UNSHIELED TWISTED PAIR-
unsheild twisted pair cable use for LAN and telephone system UTP cable are compose of four colour coded pair of copper condactr twisted arround each other and outer jacket provide protection and key the pair in aling ment UTP cable connect to device a pin modular connector told RJ45 plug all LAN protocol can oprate power UTP most model LAN device with RJ45 jacks
unsheild twisted pair cable use for LAN and telephone system UTP cable are compose of four colour coded pair of copper condactr twisted arround each other and outer jacket provide protection and key the pair in aling ment UTP cable connect to device a pin modular connector told RJ45 plug all LAN protocol can oprate power UTP most model LAN device with RJ45 jacks
COAXIAL CABLE
A Coaxial Cable Consists of as single Copper Conductor as Layer of sheilding with a ground wire can outor jacket coaxial cables are some times used for bus topologies but many LAN product cable connectvity
The ethernet LAN protocol was originaslly developpod oprate over coaxial cables
10 BASED 5/THIKNET CABLE WAS THE ORGINAL ETHERNET CABLE ARE LONGER USE IN MODERN LAN.
10BASED2/THINET CABLE
Friday, 21 August 2015
Local Area network use four types of cables
TYPES OF CABLES-
1.Coaxial cable
2.Unsheiled twisted Pair (UTP)
3.Sheiled twisted Pair (STP)
4.Fiber optic
1.Coaxial cable
2.Unsheiled twisted Pair (UTP)
3.Sheiled twisted Pair (STP)
4.Fiber optic
CABLING
CABLING-
LOCAl AREA NETWORK CABLING-
The earlist LAN used coaxial cables.Over time the twisted pair cables used in telephone systems were improved to carry higher frequencles and support LAN trraffic more recently .fiber obtic cables have emerged as a high speed cabling option
LOCAl AREA NETWORK CABLING-
The earlist LAN used coaxial cables.Over time the twisted pair cables used in telephone systems were improved to carry higher frequencles and support LAN trraffic more recently .fiber obtic cables have emerged as a high speed cabling option
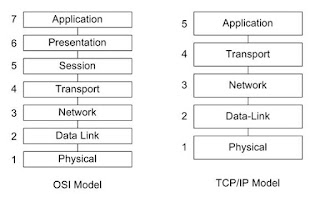
TCP/IP MODEL -
The late gos the defense advance research project agency (DARPA) origianally developed
transmisson control protocol/ internet protocol
internet connect various depence department computer network
the internet and international wide area network
uses tcp/ip to connect network accross the world
The late gos the defense advance research project agency (DARPA) origianally developed
transmisson control protocol/ internet protocol
internet connect various depence department computer network
the internet and international wide area network
uses tcp/ip to connect network accross the world
Thursday, 20 August 2015
OSI MODEL
1.researced and developed by the ISO- (INTER ORANIZITION FOR STANDARDIZATIONS)
2.1977 establish a subcommit to develope a communition architecture
3.1984 publish iso 7498 the open system interconnection osi reference model
THE OSI MODEL A FRAME WORK WITHIN WHICH NETWORKING STANDARDS CAN BE DEVELOPED IT PROVIDED VENDORS WITH A SET A STANDARDS THAT ENSURED GREATER COMPABILTIY
AND BETWEEN THE VARIOUS TYPES OF NETWORK TECHNOLOGIES THAT WERE PRODECER BY THE MANY COMPANIES AROUND THE WORLD
Q-WHY A LAYERED MODEL ?
+reduce complexity
+ standardizes interfaces
+ facilitates modular engineering
+ensure interoperable technology
+ accelerates evolation
+simplifies teachning and learning
What is internet,interanet,extranet?
INTERNET
1.internet is a network of network a network to be called as internet any unknown external user or user or users are allowed to access the part of resources of the network.
2.when you want to expose information to everyone in the world then we use internet protocol such as HTTP,FTP,SMTP, it is a example of internet
INTRANET
1.an intranet is a private N/w
2.it can be a collection of LAN ,MAN,&WAN
3.users access the resources from with in the oraganzition (locally)
4.if it within company's intranet the information
would not be access ible to person on the internet
it is for private use only
EXTRANET
1.extranet is a extended intranet
2.some service are made available to known users or bussiness partner
3.they can access resource from outside the organization (remotely) like home or office
4.in intranet users access the resources from within the organization while in a extranet some known users are allowed to access the resources from the outsides network
5.if we have a web based application that allows selected outside bussness partners to review their accounts that is called extranets
1.internet is a network of network a network to be called as internet any unknown external user or user or users are allowed to access the part of resources of the network.
2.when you want to expose information to everyone in the world then we use internet protocol such as HTTP,FTP,SMTP, it is a example of internet
INTRANET
1.an intranet is a private N/w
2.it can be a collection of LAN ,MAN,&WAN
3.users access the resources from with in the oraganzition (locally)
4.if it within company's intranet the information
would not be access ible to person on the internet
it is for private use only
EXTRANET
1.extranet is a extended intranet
2.some service are made available to known users or bussiness partner
3.they can access resource from outside the organization (remotely) like home or office
4.in intranet users access the resources from within the organization while in a extranet some known users are allowed to access the resources from the outsides network
5.if we have a web based application that allows selected outside bussness partners to review their accounts that is called extranets
Wednesday, 19 August 2015
MESH TOPOLOGY
IN THIS TOPOLOGY EACH COMPUTER BY USING A SEPARATE CABLE SEGMENT THEN THE TRAFFIC CAN BE RE ROUTED THREW A DIFFRENT PATH WAY BECAUSE THERE ARE MULTIPLE PATH WAYS TO SEND DATA FROM ONE SYSTEM TO ANOTHER SYSTEM .THIS TOPOLOGY IS USED TO CONNECT VARIOUS SIDES IN A N/W TO ESTABLISH MULTIPLE LINKS AND USED WAN N/W
IN THIS TOPOLOGY EACH COMPUTER BY USING A SEPARATE CABLE SEGMENT THEN THE TRAFFIC CAN BE RE ROUTED THREW A DIFFRENT PATH WAY BECAUSE THERE ARE MULTIPLE PATH WAYS TO SEND DATA FROM ONE SYSTEM TO ANOTHER SYSTEM .THIS TOPOLOGY IS USED TO CONNECT VARIOUS SIDES IN A N/W TO ESTABLISH MULTIPLE LINKS AND USED WAN N/W
Subscribe to:
Comments (Atom)